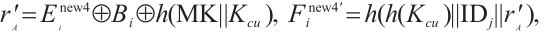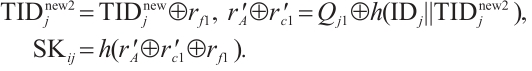| Issue |
Wuhan Univ. J. Nat. Sci.
Volume 29, Number 3, June 2024
|
|
|---|---|---|
| Page(s) | 209 - 218 | |
| DOI | https://doi.org/10.1051/wujns/2024293209 | |
| Published online | 03 July 2024 | |
Computer Science
CLC number: TP309.2
Analysis and Improvement of an Authentication Scheme for Fog Computing Services
1
School of Software, Tiangong University, Tianjin 300387, China
2
School of Computer Science and Technology, Tiangong University, Tianjin 300387, China
† Corresponding author. E-mail: baoyuankang@aliyun.com
Received:
28
September
2023
Fog computing utilizes devices in the edge network to transmit data with very low latency and supports high mobility. However, fog computing inherits security and privacy problems from cloud computing. Therefore, various privacy schemes for fog computing have been proposed to prevent different types of attacks. Recently, Weng et al proposed a fog computing authentication scheme; after analyzing, we found that Weng et al's scheme cannot resist user tracking attack and user impersonation attack. Then, we propose an improved scheme through adding a password, modifying the calculation method of Ei, and adding timestamps. In addition, we also compare the improved scheme with existing authentication schemes in terms of security and computational efficiency. The results show that the improved scheme is more secure and has less computation.
Key words: authentication scheme / fog computing / security
Cite this article: HUO Yuyan, KANG Baoyuan, NIU Shufang, et al. Analysis and Improvement of an Authentication Scheme for Fog Computing Services[J]. Wuhan Univ J of Nat Sci, 2024, 29(3): 209-218.
Biography: HUO Yuyan, female, Master candidate, research directions: cryptography. E-mail: yuyanhuo@aliyun.com
© Wuhan University 2024
 This is an Open Access article distributed under the terms of the Creative Commons Attribution License (https://creativecommons.org/licenses/by/4.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
This is an Open Access article distributed under the terms of the Creative Commons Attribution License (https://creativecommons.org/licenses/by/4.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
0 Introduction
Cloud computing is a business computing model. It distributes computer tasks to resource pools made up of large numbers of computers, enabling various applications to obtain computing power, storage space, and information services as needed. However, compared with traditional decentralized computing, cloud computing centralizes computing resources, and risks are centralized together. Therefore, cloud computing cannot meet the needs of high mobility, location-aware, and low-latency applications [1]. Fog computing was born to eliminate the limitations of cloud computing and is used to be a link between the Internet of Things devices and the cloud [1]. In fog computing, fog services are distributed at the margin of the network and close to terminal equipment geographically [2], so some data can be processed and stored directly in the fog layer. As a result, fog computing can reduce the pressure on the cloud, improve transmission rates, and reduce latency.
Fog computing can effectively decentralize computational and analytical power and help reduce bandwidth usage. However, fog nodes are often deployed in remote and unprotected places [3], and rely on insecure public channels for data transmission between users and fog servers, as well as fog servers and cloud servers. Therefore, secure identity authentication is critical in fog computing.
Many researchers have recently proposed identity authentication schemes in fog computing environments. Lampot first proposed a remote authentication scheme in an insecure environment in 1981[4]. Then, many two-factor authentication schemes based on Hashes, smart cards, and temporary certificates were proposed[5-10], but most of them have security issues. Then, lots of three-factor authentication schemes[1,11-15] based on fog computing were proposed. In 2019, Ma et al[16] proposed an authenticated key agreement protocol without bilinear pairing and claimed that their scheme achieves mutual authentication, generates a securely agreed session key for secret communication, and supports privacy protection. In 2021, Chen et al [17] proposed an authenticated key exchange scheme for fog computing. However, after analysis, Rana et al[18] found that Chen et al's scheme [17] does not provide user anonymity and is also not resistant to tamper-proof device stolen attack, user impersonation attack, fog node impersonation attack, insider attack, and known session key attack. In 2021, Weng et al [15] proposed a lightweight anonymous mutual authentication and secure communication scheme and claimed that their scheme only uses one-way Hash functions, and XOR operations and security can be ensured.
In this paper, we point out the shortcomings of Weng et al's [15] scheme. Weng et al's scheme cannot resist user traceability attack and user impersonation attack. Therefore, we propose an improved scheme through adding a password, modifying the calculation method of Ei, and adding timestamps. We also compare security features and computation costs between the improved scheme and the other four schemes[3, 15-17].
The rest of the paper is structured as follows: Section 1 briefly reviews Weng et al's scheme. Section 2 analyses the shortcomings of Weng et al's scheme. In Section 3, an improved scheme is presented. Section 4 provides a security analysis and comparison of the enhanced scheme. Section 5 concludes the paper.
1 Review of Weng et al's Scheme
In Weng et al's scheme [15], there are two mutual authentication and key agreement phases: one is the authentication and key agreement phase of edge user EUi and fog server FSj, and the other is the authentication and key agreement phase of edge device EDk and fog server FSj. Through analysis, we find that the two phases similarly implement mutual authentication and key agreement. So, in this section, we only review the authentication and key agreement phase of edge user EUi and fog server FSj. There are three participants in Weng et al's scheme: cloud server, fog servers, and edge users. Fog servers and edge users all register to the cloud server, and then edge users and fog servers authenticate with each other and agree on the same session keys with the help of the cloud server. Weng et al's scheme [15] consists of the following steps. The notations used in this article are listed in Table 1.
Notations table
1.1 System Initialization
The cloud server CS generates a master secret key MK, and two long-term secret keys Kcf and Kcu, and keeps them secret. CS chooses a one-way Hash function h(·).
1.2 Fog Server Registration Phase
Fog server FSj selects a unique identity IDj and sends identity IDj to CS via a secure channel. On receiving IDj, CS generates a pseudonym TIDj, and computes
Then CS sends {TIDj, Bj, h(MK||Kcf)} to FSj and maintains {TIDj, IDj, Bj} in a protected verifier table of FSj. Finally, FSj stores TIDj, Bj, and h(MK||Kcf) in its memory.
1.3 Edge User Registration Phase
Edge user EUi selects a unique identity IDi and imprints his/her biometric BIOi into smart device MDi. MDi generates a 160-bit random secret number nu and computes Ai=h(IDi||BIOi||nu). Then MDi sends {Ai,IDi} to CS through a secure channel. After receiving IDi and Ai, CS generates a pseudonym TIDi, and computes
Then CS sends  to EUi via a secure channel and maintains
to EUi via a secure channel and maintains  in a protected verifier table of EUi. Finally, EUi's smart device stores
in a protected verifier table of EUi. Finally, EUi's smart device stores  in its memory.
in its memory.
1.4 Authentication and Key Agreement Phase
In this phase, an edge user EUi wants to access a fog server FSj through a public channel, the cloud server CS can help EUi and FSj to authenticate each other and achieve a session key SKij. The specific steps are as follows.
Step 1: EUi first inputs  and
and  into his/her smart device. Then, MDi retrieves nu and h(Kcu) to compute
into his/her smart device. Then, MDi retrieves nu and h(Kcu) to compute
and checks whether  . If it is true, it means EUi is a legal user, then smart device MDi selects a 128-bit random number ru and computes
. If it is true, it means EUi is a legal user, then smart device MDi selects a 128-bit random number ru and computes
Finally, MDi sends the message  to FSj through a public channel.
to FSj through a public channel.
Step 2: On receiving Mu1, FSj selects a 128-bit random number rf and retrieves TIDj, Bj, and h(MK||Kcf ) to compute
Finally, FSj sends messages Mu1 and Mu2 = {TIDj, Oj, Pj} to CS through a public channel.
Step 3: On receiving Mu1 and Mu2, CS inspects Mu1 and searches the verifier table of EUi in its database to find entry that match TIDi. If there is no matching entry, CS rejects the request and terminates the session. Otherwise, CS retrieves Bi and h(MK||Kcu) to compute
Then CS checks whether  If it is not true, CS terminates the session. Otherwise, the legitimacy of EUi is authenticated by CS.
If it is not true, CS terminates the session. Otherwise, the legitimacy of EUi is authenticated by CS.
Step 4: CS further inspects Mu2 and searches the verifier table of FSj in its database to find entry that match TIDj. If there is no matching entry, CS rejects the request and terminates the session. Otherwise, CS retrieves Bj and h(MK||Kcf ) to compute
Then CS checks whether 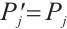 .
.
Step 5: After verifying the validity of EUi and FSj, CS refreshes pseudonyms for EUi and FSj by computing
And CS replaces TIDi with  in the verifier table of EUi, replaces TIDj with
in the verifier table of EUi, replaces TIDj with  in the verifier table of FSj. CS further selects a 128-bit random number rcand computes
in the verifier table of FSj. CS further selects a 128-bit random number rcand computes
Finally, CS sends Mu3 = {Qj, Rj} and Mu4 = {Sj, Tj} to FSj.
Step 6: On receiving Mu3 and Mu4, FSj computes
FSj checks if  . Finally, FSj sends Mu4 to EUi.
. Finally, FSj sends Mu4 to EUi.
Step 7: On receiving Mu4, EUi computes
If  , EUi believes that CS and FSj are legal parties and stores the shared session key SKij for future secure communication.
, EUi believes that CS and FSj are legal parties and stores the shared session key SKij for future secure communication.
2 Attacks on Weng et al's Scheme
This section will show that Weng et al's scheme[15] is vulnerable to user traceability and impersonation attacks. Further details are provided in the following subsections.
2.1 User Traceability Attack
Weng et al's scheme[15] cannot resist user traceability attack. The following steps show the process of user traceability attack.
Step 1:In the first authentication, if a user EUi sends a message MU1= trying to contact a fog server FSj, one attacker may intercept the message MU1, and then he/she saves {Ei, TIDi}. At the end of this authentication, the cloud server CS and the user will update the pseudonym by (1). Lastly, the first authentication ends.
trying to contact a fog server FSj, one attacker may intercept the message MU1, and then he/she saves {Ei, TIDi}. At the end of this authentication, the cloud server CS and the user will update the pseudonym by (1). Lastly, the first authentication ends.
But through (1) and (2), the attacker can know
Step 2:In the second authentication, assume that three users EUA, EUB, EUC, and the same user EUi all send messages trying to contact a fog server FSg. EUA sends message MU1a= , EUB sends message MU1b=
, EUB sends message MU1b= , EUC sends message MU1c=
, EUC sends message MU1c= and EUi sends message MU1i=
and EUi sends message MU1i= , the attacker intercepts four messages MU1a, MU1b, MU1c, MU1i and uses the previous intercepted Ei and TIDi to calculate
, the attacker intercepts four messages MU1a, MU1b, MU1c, MU1i and uses the previous intercepted Ei and TIDi to calculate
The attacker also saves the intercepted messages MU1a, MU1b, MU1c and MU1i. At the end of the second authentication, the new pseudonym of user EUi has been updated to  .
.
Step 3: In the third authentication, assume that three users EUJ, EUK, EUL and the same user EUi send messages trying to contact a fog server FSl. The four users send messages 
 , respectively. The attacker intercepts all four messages MU1j, MU1k, MU1l, and
, respectively. The attacker intercepts all four messages MU1j, MU1k, MU1l, and  and according to the second intercepted messages MU1a, MU1b, MU1c and MU1i to calculate
and according to the second intercepted messages MU1a, MU1b, MU1c and MU1i to calculate
After calculating (4) and (5), the attacker will find that Nd = Nii. This is because  where Ai and Di are constant, then the attacker can determine the messages MU1, MU1i and
where Ai and Di are constant, then the attacker can determine the messages MU1, MU1i and  are from the same user EUi. When a user EUk contacts a fog server FSn with the new pseudonym
are from the same user EUi. When a user EUk contacts a fog server FSn with the new pseudonym  next time, the attacker can judge whether EUk is EUi by calculating
next time, the attacker can judge whether EUk is EUi by calculating  . Thus, user traceability attack can be successful.
. Thus, user traceability attack can be successful.
2.2 User Impersonation Attack
Weng et al's scheme[15] cannot resist user impersonation attack and the attack can be simulated as follows.
Step 1: According to the Section 2.1, the attacker can obtain the value of  of edge user EUi. Based on user traceability attack, the attacker intercepts the message
of edge user EUi. Based on user traceability attack, the attacker intercepts the message  sent by EUi to the fog server. According to (6), the attacker can calculate the random number
sent by EUi to the fog server. According to (6), the attacker can calculate the random number  chosen by edge user EUi this time; then, the attacker can calculate the new pseudonym updated by the user and cloud server CS at the end of this authentication by (7).
chosen by edge user EUi this time; then, the attacker can calculate the new pseudonym updated by the user and cloud server CS at the end of this authentication by (7).
Step 2: Assume that the attacker is a legitimately registered user, then, based on the analysis in Step 1, the attacker can know 
 h(Kcu). In the login and authentication phase, the attacker selects a fog server FSj that he/she wants to contact and picks a random number rA , calculates
h(Kcu). In the login and authentication phase, the attacker selects a fog server FSj that he/she wants to contact and picks a random number rA , calculates
Then, the attacker sends the message  to the fog server FSj.
to the fog server FSj.
Step 4: Upon receiving the message  , FSj chooses a random number rf1, and calculates
, FSj chooses a random number rf1, and calculates
FSj sends the message  to the cloud server CS, where
to the cloud server CS, where  is the fog server FSj's pseudonym.
is the fog server FSj's pseudonym.
Step 5: On receiving messages  CS first checks the validity of pseudonyms; it is evident that
CS first checks the validity of pseudonyms; it is evident that  ,
, is valid, and then CS computes
is valid, and then CS computes
This verification can pass, and the attacker can successfully impersonate user EUi. Then, cloud server CS chooses a random number rc1,and computes
Then, the cloud server CS sends MU3={Qj1, Rj1}, MU4={Sj1,Tj1} to the fog server FSj.
Step 6: After receiving MU3 and MU4 from CS, the fog server FSj computes
Step 7: The attacker can also compute the session key by
Eventually, the attacker and the fog server FSj agree on a session key SKij with the help of the cloud server CS.
3 The Improved Scheme
To overcome the shortcomings of Weng et al's scheme[15], we propose an improved scheme in this section. In the registration phase, we add a password to make the improved scheme more complete, and we also avoid sending h(kcu) and h(MK||Kcf) directly, this can prevent attackers from performing impersonation attack. In the login and authentication phase, to ensure that the improved scheme is resistant to user traceability attack, we also modify the calculation of Ei and add timestamps. The following is a detailed description of the improved scheme.
3.1 Deployment Phase
The cloud server CS generates a master secret key MK and two long-term secret keys Kcf and Kcu and keeps them secret. CS chooses a one-way Hash function h(·).
3.2 Fog Server Registration Phase
Fog server FSj selects a unique identity IDj and registers itself with CS by sending identity IDj to CS via a secure channel. On receiving IDj, CS generates a pseudonym TIDj and a random secret number nf and computes  and
and  CS publicizes fog server FSj's identity IDj. Then CS sends {TIDj,Bj,h(MK||Kcf ||nf)} to FSj and maintains {TIDj, IDj, Bj, nf} in a protected verifier table. Finally, FSj stores TIDj, Bj, and h(MK||Kcf ||nf) in its memory. The fog server registration phase is illustrated in Fig. 1.
CS publicizes fog server FSj's identity IDj. Then CS sends {TIDj,Bj,h(MK||Kcf ||nf)} to FSj and maintains {TIDj, IDj, Bj, nf} in a protected verifier table. Finally, FSj stores TIDj, Bj, and h(MK||Kcf ||nf) in its memory. The fog server registration phase is illustrated in Fig. 1.
 |
Fig. 1 Fog server registration |
3.3 Edge User Registration Phase
Edge user EUi selects a unique identity IDi, PWi, and imprints his/her biometric BIOi into a smart device. EUi's smart device MDi generates a random secret number nu and computes
Then MDi sends {Ai, IDi, PPWi} to CS through a secure channel. After receiving IDi, Aiand PPWi, CS generates a psedonym TIDi and computes
Then CS sends  to EUi via a secure channel and maintains
to EUi via a secure channel and maintains  in a protected verifier table. Finally, MDi computes
in a protected verifier table. Finally, MDi computes
Then, MDi stores  in its memory. Edge user registration phase is explained in Fig. 2.
in its memory. Edge user registration phase is explained in Fig. 2.
 |
Fig. 2 Edge user registration |
3.4 Authentication and Key Agreement Phase
In this phase, if an edge user EUi wants to access a fog server FSj through a public channel, EUi and FSj authenticate each other with the help of the cloud server CS and establish a session key SKij. The detailed steps are as follows and the detailed process is explicated in Fig. 3.
 |
Fig. 3 Authentication and key agreement phase |
Step 1: EUi first inputs  and imprints
and imprints  into his/her smart device MDi. Then, MDi computes
into his/her smart device MDi. Then, MDi computes
checks whether  . If it does not hold, the smart device MDi rejects the request and terminates the session. Otherwise, it means that this user is a legitimate smart device holder. Then, user EUi selects a fog server FSj that he/she wants to contact, selects a random number ru, and generates a current timestamp T1. MDi computes
. If it does not hold, the smart device MDi rejects the request and terminates the session. Otherwise, it means that this user is a legitimate smart device holder. Then, user EUi selects a fog server FSj that he/she wants to contact, selects a random number ru, and generates a current timestamp T1. MDi computes
Finally, MDi sends the request message  to FSj through a public channel.
to FSj through a public channel.
Step 2: On receiving Mu1, FSj first checks the freshness of the message. Then, FSj selects a random number rf and a current timestamp T2, and retrieves TIDj, Bj, and h(MK||Kcf ||nf) to compute
Finally, FSj sends messages Mu1 and Mu2 ={TIDj, Mj, Vj, T2} to CS through a public channel.
Step 3: On receiving Mu1 and Mu2, CS first checks the freshness of the messages. If true, CS retrieves Bi, Hi and Bj, IDj, nf according to TIDi and TIDj, respectively. Then CS computes
CS checks whether  . If it is not true, CS terminates the session. Otherwise, the legitimacy of EUi is authenticated by CS. CS further computes
. If it is not true, CS terminates the session. Otherwise, the legitimacy of EUi is authenticated by CS. CS further computes
Then CS checks whether  .
.
Step 4: After verifying the validity of EUi and FSj, CS refreshes new pseudonyms for EUi and FSj by computing
and replaces TIDi with  in the verifier table of EUi, replaces TIDj with
in the verifier table of EUi, replaces TIDj with  in the verifier table of FSj. CS further selects a random number rc and a current timestamp T3 to compute
in the verifier table of FSj. CS further selects a random number rc and a current timestamp T3 to compute
Finally, CS sends Mu3 ={Hj, Ij, T3} and Mu4 ={Ji, Ki, T3} to FSj.
Step 5: On receiving Mu3 and Mu4, FSj computes
FSj checks if  . If it holds, FSj sends Mu4 to EUi.
. If it holds, FSj sends Mu4 to EUi.
Step 6: On receiving Mu4, EUi computes
If  , EUi believes that CS and FSj are legal parties and stores the shared session key SKij for future secure communication. Then, EUi computes
, EUi believes that CS and FSj are legal parties and stores the shared session key SKij for future secure communication. Then, EUi computes
and replaces  with
with  in smart device's memory.
in smart device's memory.
4 Security Analysis and Comparisons
4.1 Security Analysis
This section analyzes security of the improved scheme. We demonstrate the improved scheme's security features and resilience against various attacks.
4.1.1 User anonymity
The improved scheme has strong anonymity. During the authentication and key agreement phase, the edge user's identity is never shared openly or sent over the public channel; instead, the edge user sends his/her pseudonym TIDi. Even if an attacker intercepts the edge user's pseudonym TIDi, he/she cannot know the user's identity IDi.
4.1.2 Password guessing attack
Assuming that an attacker gets all information  stored in the mobile device, the attacker performs password guessing attack based on
stored in the mobile device, the attacker performs password guessing attack based on  . However, the attacker must know the values of PPWi and nu. Although the attacker knows the value of nu, he/she cannot know the value of PPWi. So, the attacker cannot guess the password.
. However, the attacker must know the values of PPWi and nu. Although the attacker knows the value of nu, he/she cannot know the value of PPWi. So, the attacker cannot guess the password.
4.1.3 Replay attack
An attacker may resend previous messages to cloud server for replay attack. However, this will not succeed because the improved scheme contains timestamp verifications, and the timestamps in past messages are not within an acceptable range. Resending past messages will cause the session to terminate. Even if an attacker can modify the timestamp T1, the attacker does not know Di, Ai, and h(Kcu||PPWi), then the corresponding values Mi and Vi cannot be modified based on the new timestamp. Finally, the value of Vi sent by the attacker differs from  calculated by the cloud server CS by (8), and verification
calculated by the cloud server CS by (8), and verification  cannot pass. Therefore, the improved scheme can resist replay attack.
cannot pass. Therefore, the improved scheme can resist replay attack.
4.1.4 User untraceability
In the mutual authentication and key agreement phase, the user's identity is hidden by sending the pseudonym TIDi, and the user's pseudonym TIDi is updated every time by (9). Due to the inclusion of random number ru in (9), the user's pseudonym will be different each time. Therefore, the attacker does not know what the user's next pseudonym  will be.
will be.
When the attacker intercepts EUi's request message Mu1={TIDi,Mi,Vi,T1}, and stores {TIDi, Mi} as described in Section 2.1.
In the second authentication, even if the attacker intercepts EUi's message 
 , the attacker computes
, the attacker computes
In the third authentication, assuming that the attacker intercepts EUi's request message 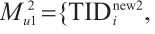
 once again, the attacker computes
once again, the attacker computes
Because  and
and  contain timestamps
contain timestamps  which makes the value of
which makes the value of 
 is not equal to the value of
is not equal to the value of  . Therefore, even if the attacker intercepts messages from the same user EUi, the result of
. Therefore, even if the attacker intercepts messages from the same user EUi, the result of  will be different every time, and the user traceability attack cannot be performed.
will be different every time, and the user traceability attack cannot be performed.
4.1.5 User impersonation attack
If an attacker intercepts  sent by edge user EUi on the public channel and assumes that the attacker obtains the user's data stored in the mobile device's memory
sent by edge user EUi on the public channel and assumes that the attacker obtains the user's data stored in the mobile device's memory  , if an attacker wants to impersonate the user to spoof the cloud server successfully, he/she must construct new Mi and Vi based on (10) and (11), so that the verification of the Vi can pass. Still, the attacker cannot construct a correct Mi and Vi, because the attacker cannot obtain the values of Di, Ai, and h(Kcu||PPWi). Therefore, the attacker cannot impersonate an edge user.
, if an attacker wants to impersonate the user to spoof the cloud server successfully, he/she must construct new Mi and Vi based on (10) and (11), so that the verification of the Vi can pass. Still, the attacker cannot construct a correct Mi and Vi, because the attacker cannot obtain the values of Di, Ai, and h(Kcu||PPWi). Therefore, the attacker cannot impersonate an edge user.
4.1.6 Session key agreement
The improved scheme can achieve secure session key agreement. Edge user, fog server, and the cloud server CS can compute a shared session key  . And the attacker cannot compute the correct session key because the random numbers ru, rf and rc chosen by the three entities are protected by (12), (13), (14), (15); the attacker does not know the value of the random number ru, rf and rcin the session key, so security of the session key in the improved scheme is guaranteed.
. And the attacker cannot compute the correct session key because the random numbers ru, rf and rc chosen by the three entities are protected by (12), (13), (14), (15); the attacker does not know the value of the random number ru, rf and rcin the session key, so security of the session key in the improved scheme is guaranteed.
4.1.7 Mutual authentication
In the improved scheme, edge users, fog servers, and the cloud server can authenticate each other's identity. For example, the cloud server can authenticate the edge user's identity through the verification of Viin (16), because the calculation of Vi includes h(Kcu||PPWi), only edge user EUi and the cloud server CS know the value of h(Kcu||PPWi). Cloud server CS authenticates the fog server's identity via Vj in (17), because only fog server FSj and CS know the value of  Therefore, the attacker cannot impersonate the edge user or fog server.
Therefore, the attacker cannot impersonate the edge user or fog server.
4.1.8 Denial of service attack
The improved scheme can resist denial of service attack. If an attacker wants to waste network resources for DOS attack, his fake messages must pass a verification. However, according to our analysis above, if the attacker impersonates user EUi and sends messages to CS, this fake messages cannot pass the verification of Vi. Even if the attacker changes the timestamp, he/she cannot calculate the correct Mi, Vi, and Vj based on the changed timestamp. Therefore, Vi and Vj constructed by the attacker fail to pass the verification of the cloud server.
4.1.9 Perfect forward security
EUi and FSj negotiate the session key  , where ru, rf, and rc are all random numbers. The attacker cannot compute the correct session key because he/she does not know the values of the random numbers ru, rf,and rcin the session key. The attacker cannot compute the following session key based on present random numbers, and if this session key is compromised, it does not affect the security of past and future session keys.
, where ru, rf, and rc are all random numbers. The attacker cannot compute the correct session key because he/she does not know the values of the random numbers ru, rf,and rcin the session key. The attacker cannot compute the following session key based on present random numbers, and if this session key is compromised, it does not affect the security of past and future session keys.
4.2 Comparison
This section compares the improved scheme with Weng et al's scheme [15] and the other three schemes [3,16,17]. According to Weng et al's scheme [15], some symbols (H, X, Y, F) are defined and the execution times of these operations are given in Table 2. The results of the comparison of security features and computation costs are shown in Table 3 and Table 4, respectively.
As can be seen from Table 3, the improved scheme can resist various known attacks and has higher security than Weng et al's scheme [15] and the other three schemes[3,16,17]. From Table 4, it can be seen that our improved scheme requires less computation than Jia et al' scheme[3], Chen et al's scheme[17],and Ma et al's scheme[16]. Because of the use of fuzzy extractor, the improved scheme requires more computation than Weng et al's scheme [15]. However, the improved scheme can resist various known attacks and is more secure. It is worthwhile to add some necessary computations to ensure communication security.
Approximate time required for various operations
Security comparison of different schemes
Comparison of computation costs
5 Conclusion
In this paper, we find that Weng et al's authentication scheme is not resistant to user traceability attack and user impersonation attack. We propose an improved scheme to overcome the weaknesses of Weng et al's scheme. We compare the improved scheme with several existing authentication schemes in terms of security features and calculation costs. The improved scheme not only completely overcomes the drawbacks of Weng et al's scheme but also meets the lightweight feature. Therefore, the improved scheme is suitable for use in fog computing.
References
- Hamada M, Salem S A, Salem F M. LAMAS: Lightweight anonymous mutual authentication scheme for securing fog computing environments[J]. Ain Shams Engineering Journal, 2022, 13(6): 101752-101766. [CrossRef] [Google Scholar]
- Wazid M, Das A K, Kumar N, et al. Design of secure key management and user authentication scheme for fog computing services[J]. Future Generation Computer Systems, 2019, 91(2): 475-492. [CrossRef] [Google Scholar]
- Jia X, He D, Kumar N, et al. Authenticated key agreement scheme for fog-driven IoT healthcare system[J]. Wireless Networks, 2019, 25(8): 4737-4750. [CrossRef] [Google Scholar]
- Lamport L. Password authentication with insecure communication[J]. Communications of the ACM, 1981, 24(11): 770-772. [CrossRef] [Google Scholar]
- Hwang M S, Li L H. A new remote user authentication scheme using smartcards[J]. IEEE Transactions on Consumer Electronics, 2000, 46(1): 28-30. [CrossRef] [Google Scholar]
- Juang W S. Efficient multi-server password authenticated key agreement using smart cards[J]. IEEE Transactions on Consumer Electronics, 2004, 50(4): 251-255. [CrossRef] [Google Scholar]
- Das M L. Two-factor user authentication in wireless sensor networks[J]. IEEE Transactions on Wireless Communications, 2009, 8(3): 1086-1090. [CrossRef] [Google Scholar]
- Kang B Y. Cryptanalysis on an E-voting scheme over computer network[J]. 2008 International Conference on Computer Science and Software Engineering, 2008, 3: 826-829. [NASA ADS] [CrossRef] [Google Scholar]
- Xue K, Ma C, Hong P, et al. A temporal-credential-based mutual authenticationand key agreement scheme for wireless sensor networks[J]. Journal of Network and Computer Applications, 2013, 36(1): 316-323. [CrossRef] [Google Scholar]
- Kalra S, Sood S K. Advanced password based authentication scheme for wireless sensor networks[J]. Journal of Information Security and Applications, 2015, 20: 37-46. [CrossRef] [Google Scholar]
- Arij B A, Abid M, Meddeb A. A privacy-preserving authentication scheme in an edge-fog environment[J]. ACS International Conference on Computer Systems and Applications, 2018, 2017(10): 1225-1231. [Google Scholar]
- Wu T Y, Yang L, Meng Q, et al. Fog-driven secure authentication and key exchange scheme for wearable health monitoring system[J]. Security and Communication Networks, 2021, 2021(4): 1-14. [Google Scholar]
- Guo Y M, Zhang Z F, Guo Y J. Fog-centric authenticated key agreement scheme without trusted parties[J]. IEEE Systems Journal, 2021, 15(4): 5057-5066. [NASA ADS] [CrossRef] [Google Scholar]
- Ali Z, Chaudhry S A, Mahmood K, et al. A clogging resistant secure authentication scheme for fog computing services[J]. Computer Networks, 2021, 185: 107731. [CrossRef] [Google Scholar]
- Weng C Y, Li C T, Chen C L, et al. A lightweight anonymous authentication and secure communication scheme for fog computing services[J]. IEEE Access, 2021, 9(4): 145522-145537. [NASA ADS] [CrossRef] [Google Scholar]
- Ma M M, He D B, Wang H Q, et al. An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks[J]. IEEE Internet Things, 2019, 6(5): 8065-8075. [CrossRef] [Google Scholar]
- Chen C M, Huang Y, Wang K H, et al. A secure authenticated and key exchange scheme for fog computing[J]. Enterprise Information Systems, 2021, 15(1): 1-16. [NASA ADS] [CrossRef] [Google Scholar]
- Rana M, Mahmood K, Saleem MA, et al. Towards a provably secure authentication protocol for fog-driven IoT-based systems[J]. Applied Sciences, 2023, 13(3): 1424-1424. [CrossRef] [Google Scholar]
All Tables
All Figures
 |
Fig. 1 Fog server registration |
| In the text | |
 |
Fig. 2 Edge user registration |
| In the text | |
 |
Fig. 3 Authentication and key agreement phase |
| In the text | |
Current usage metrics show cumulative count of Article Views (full-text article views including HTML views, PDF and ePub downloads, according to the available data) and Abstracts Views on Vision4Press platform.
Data correspond to usage on the plateform after 2015. The current usage metrics is available 48-96 hours after online publication and is updated daily on week days.
Initial download of the metrics may take a while.